Vulnerability Assessment Plan Template
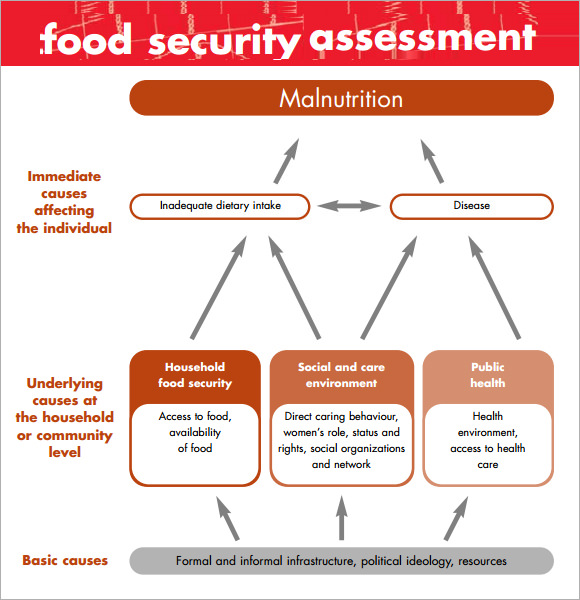
Without security and vulnerability assessments the potential exists that information systems may not be as secure as intended or desired.
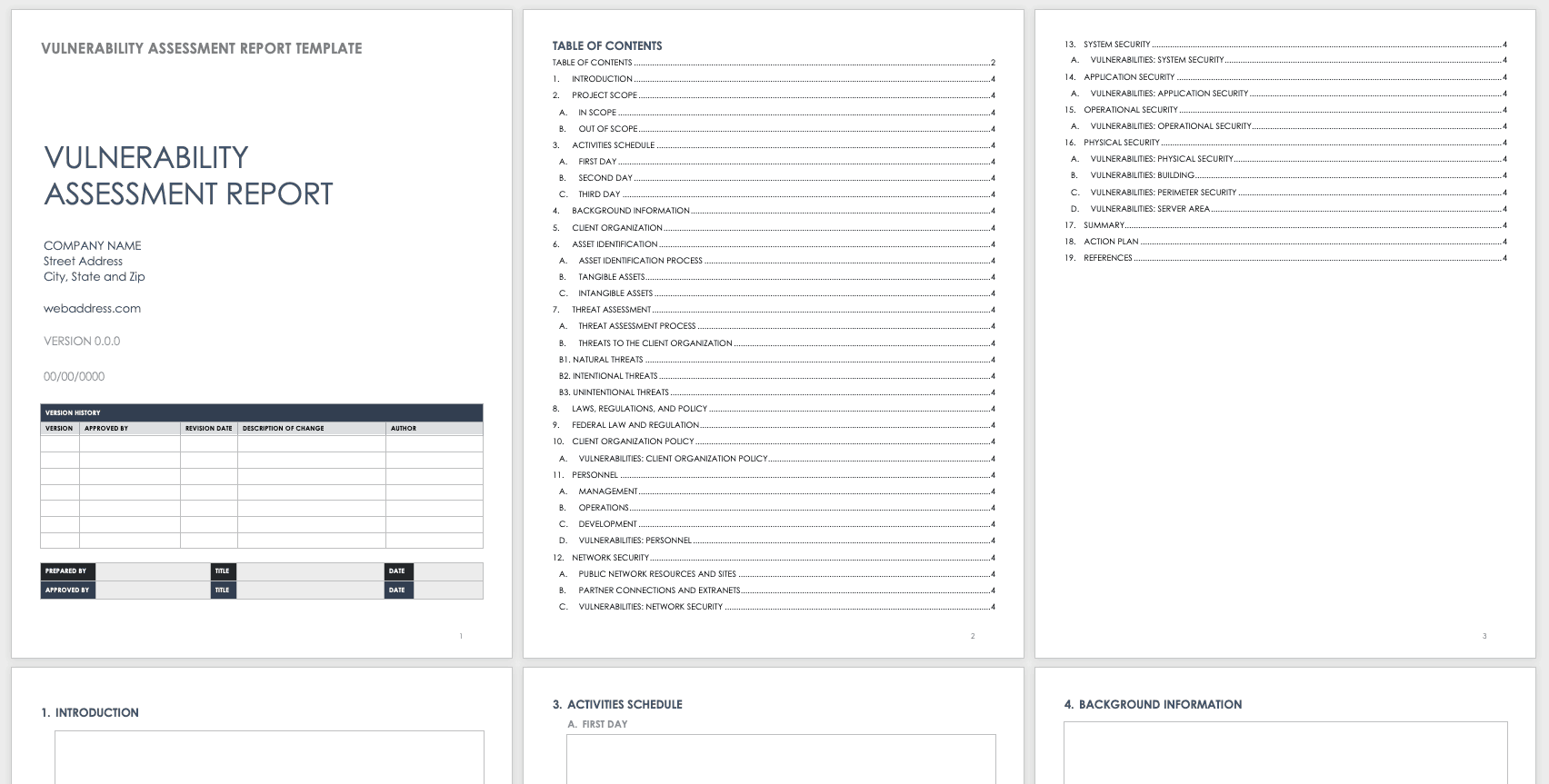
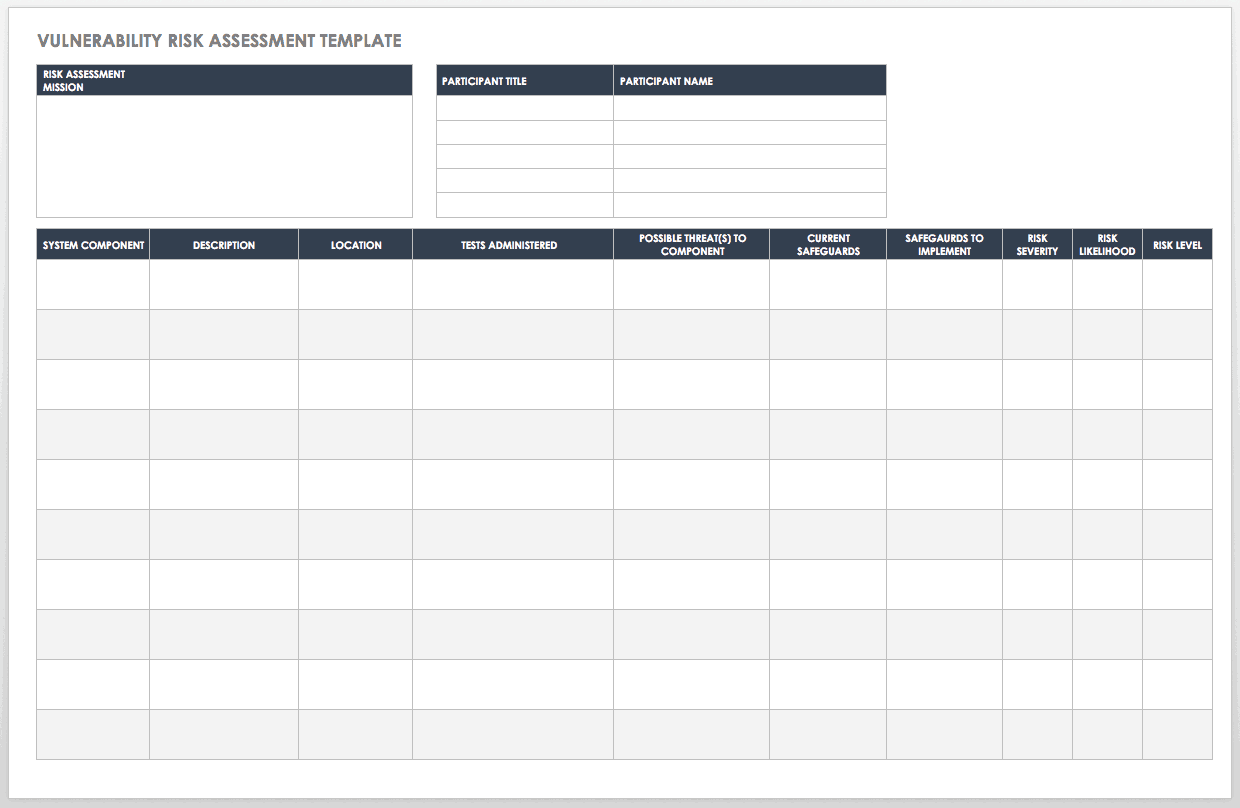
Vulnerability assessment plan template. Not only that but in a vulnerability assessment the vulnerabilities identified are also quantified and prioritized. Network based scans network based scans combine host and service discovery with vulnerability enumeration. Create a vulnerability assessment action plan template that focuses on remediation. Vulnerability assessments are.
43 assessment templates in word. This template is available in excel or google sheets formats and can be modified for a variety of assessment and planning uses whether you. This digitized template is used for conducting the initial assessment for food fraud vulnerability of a product ingredient or raw material. Andthe assessment of security and vulnerability relating to information technology is an uncertainprocess based on past.
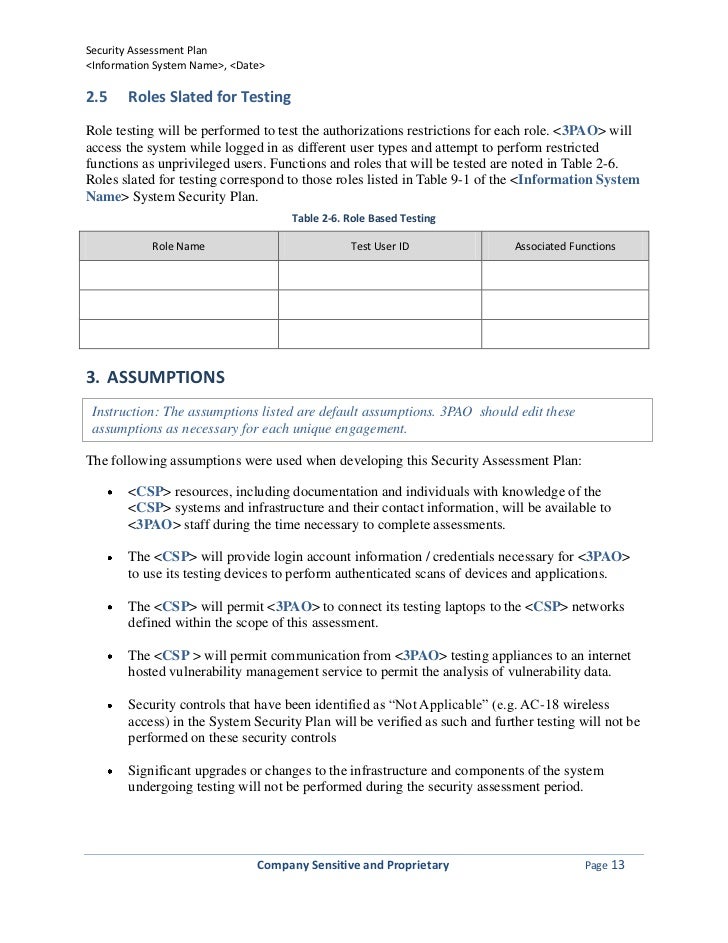
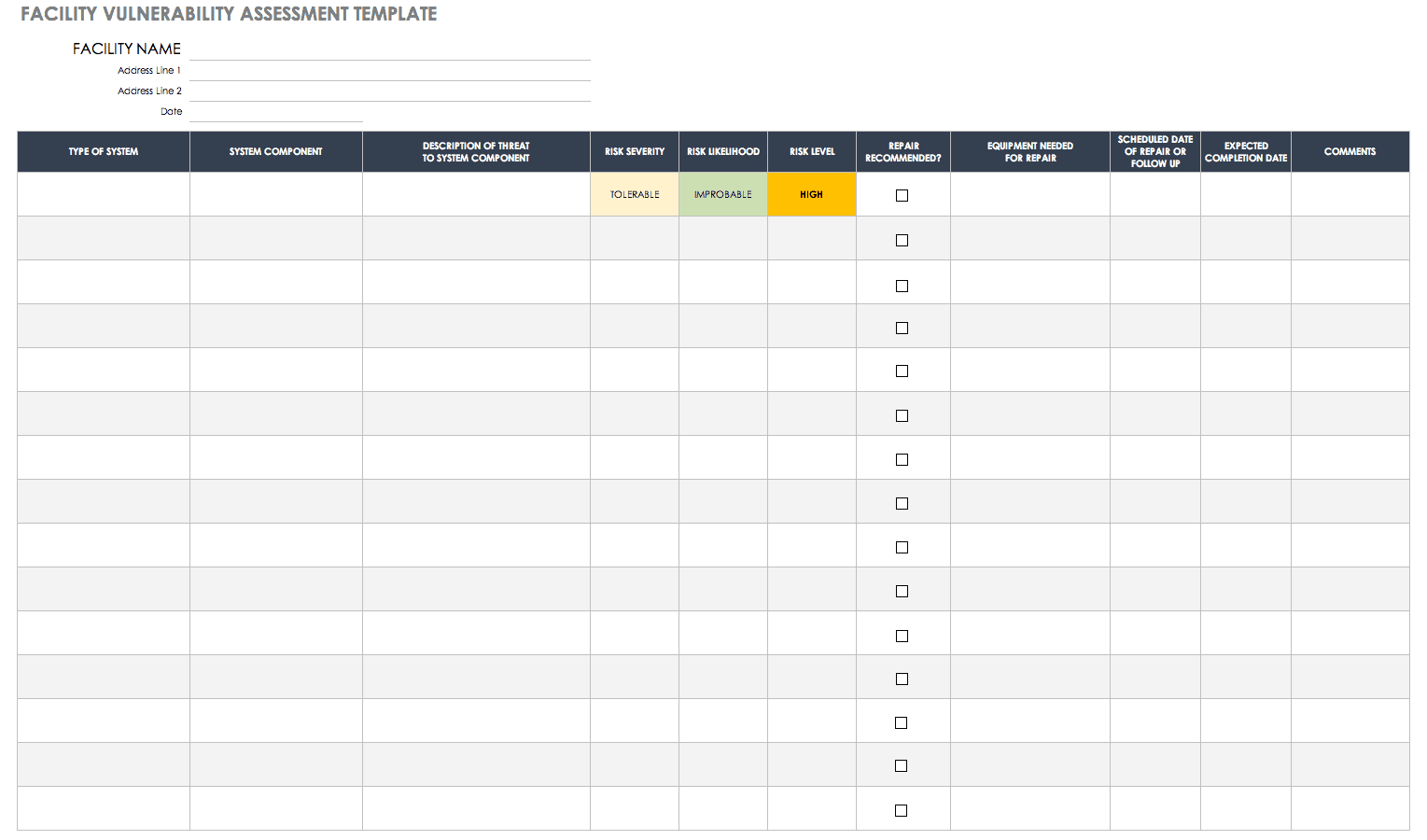
Management may decide to proceed with a facility assessment ahead of or in parallel with the assessment of environmental suitability. List weaknesses to be addressed along with remediation plans deadlines and milestones risk levels and status updates. However such an assessment is not a prerequisite of applying this template. Vulnerability assessments are done to identify the vulnerabilities of a system.
Additionally a sample is provided. Food fraud vulnerability template initial screening. Available resources for a template to complete the information classification activity. 31 assessment forms in pdf.
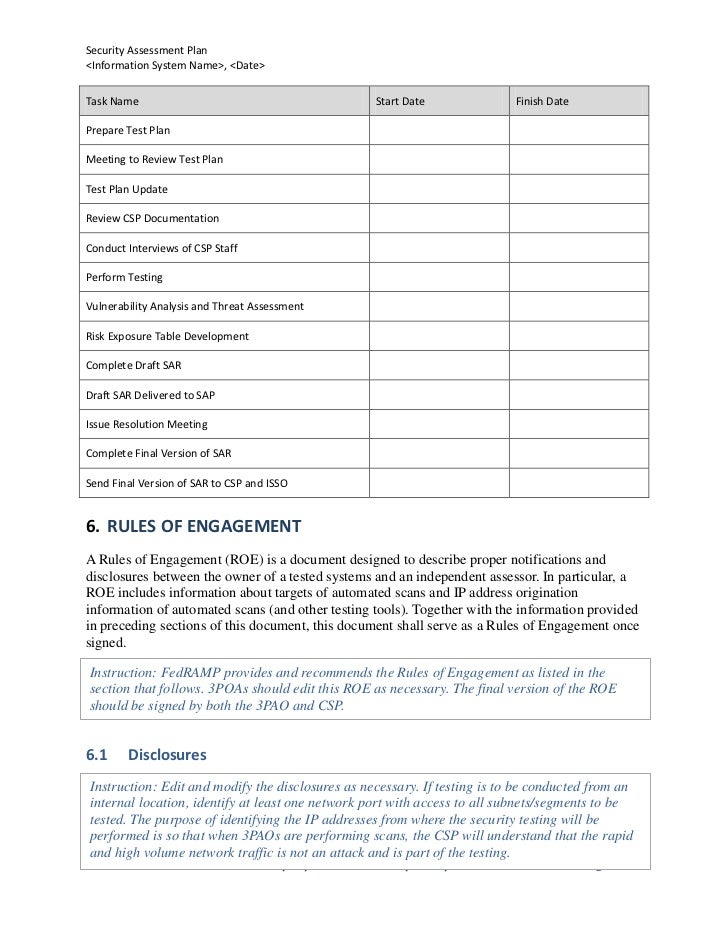
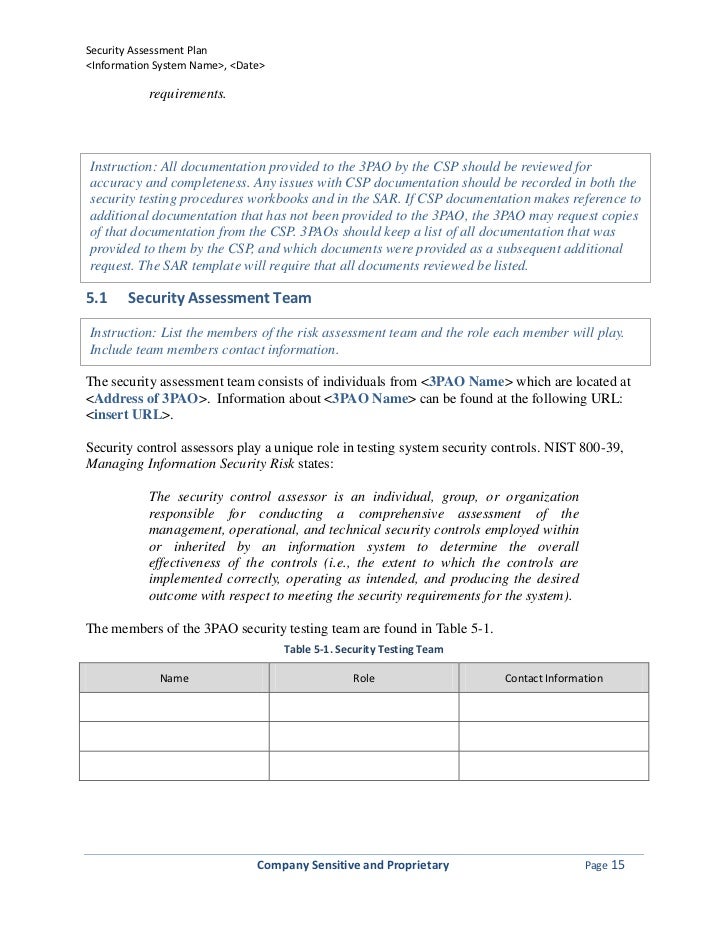
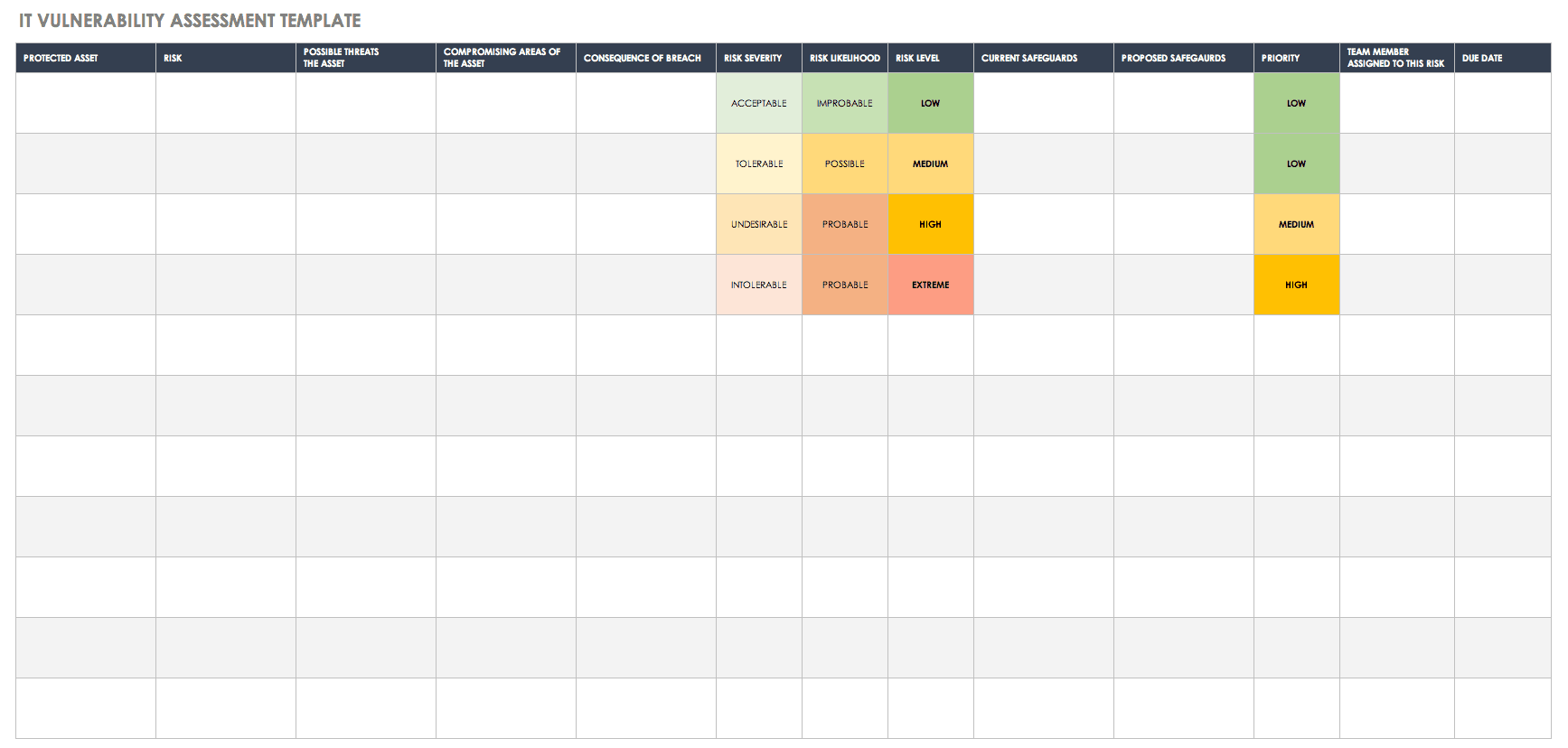
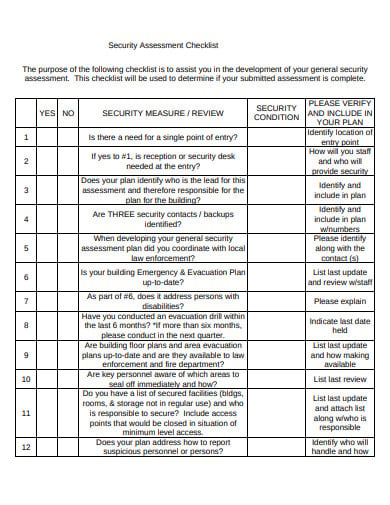
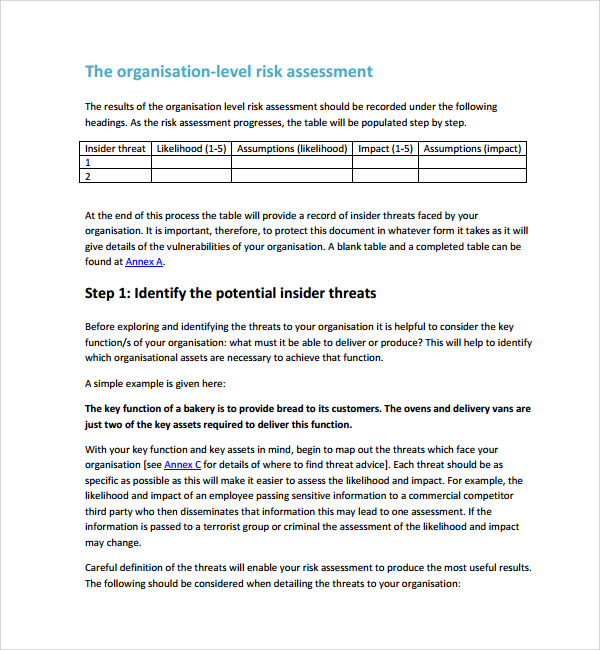
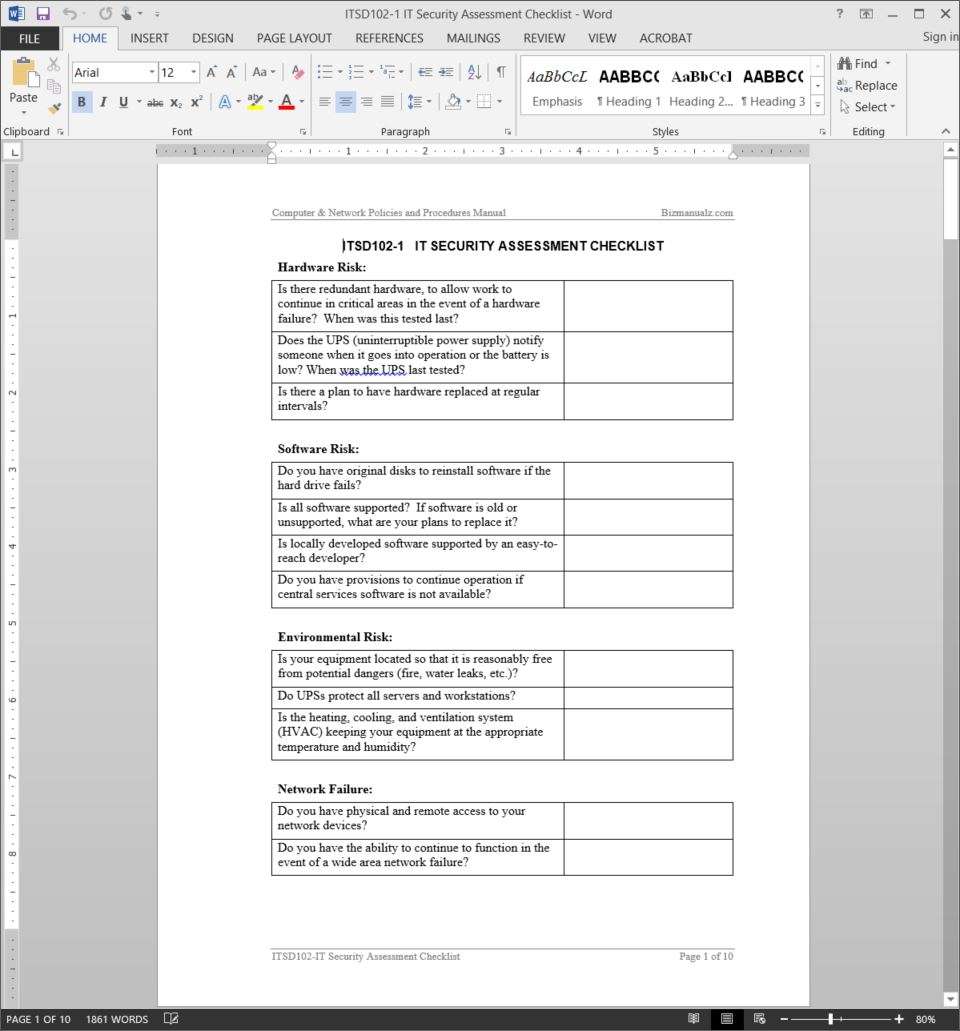
The process to plan execute and analyze results. Refer to appendix a. A vulnerability assessment is conducted to determine the weaknesses inherent in the information systems that could be exploited leading to information system breach. Information classification documents can be included within or as an attachment to the information security plan.
The template is best applied after an environmental assessment of the water source for susceptibility to mussel invasion is carried out. A vulnerability assessment is the process of identifying and analyzing those security vulnerabilities that might exist in the enterprise. The qa officer can use this digital form to proactively determine the likelihood of fraud and severity of consequences should food fraud happen. Security assessment planinformation system name date security assessment plan template version 10 may 2 2012 company sensitive and proprietary for authorized use only.