Nist 800 53 Access Control Policy Template

A full listing of assessment procedures can be found here.
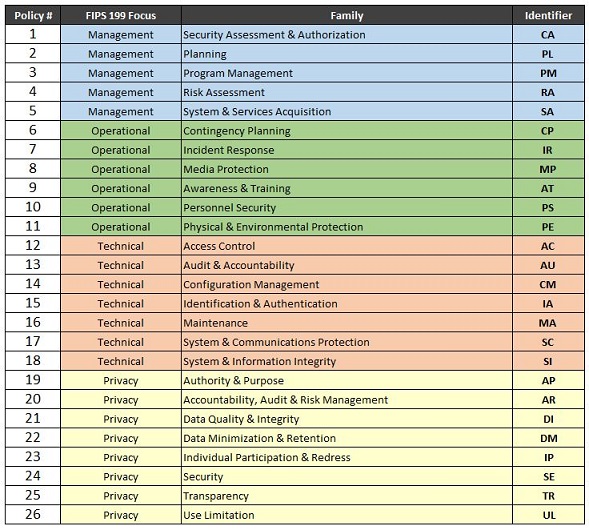
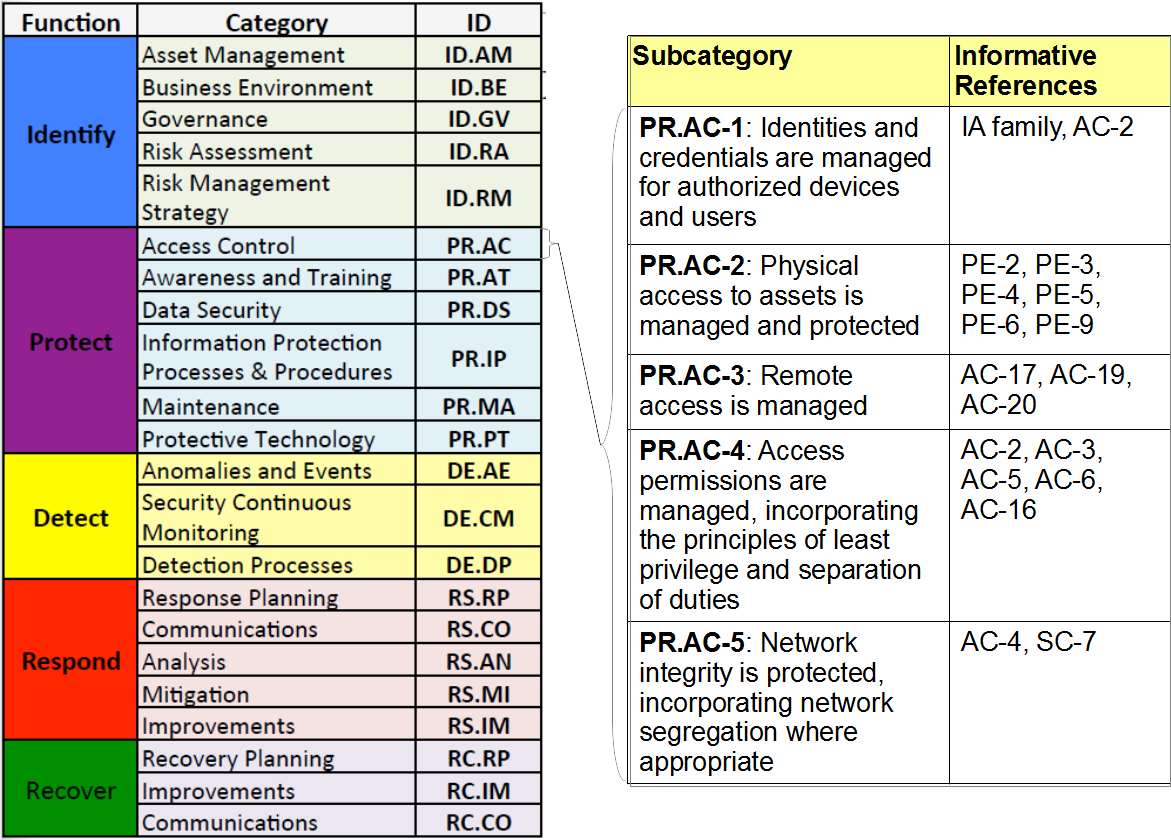
Nist 800 53 access control policy template. Procedures to facilitate the implementation of the access control policy and associated access controls. Rmf templates the purpose of nist special publication 800 53 and 800 53a is to provide guidelines for selecting and specifying security controls and assessment procedures to verify compliance. Access control procedures can be developed for the security program in general and for a particular information system when required. This publication provides a catalog of security and privacy controls for federal information systems and organizations and a process for selecting controls to protect organizational operations including mission functions image and reputation organizational assets individuals other organizations and the nation from a diverse set of threats including hostile cyber attacks natural.
Higher education institutions continue to refine their understanding of the impact of nist special publication 800 171 on their it systems and the data they receive from the federal governmentthis compliance template will help institutions map the nist sp 800 171 requirements to other common security standards used in higher education and provides suggested responses to controls. Pe 33 physical access. Executive orders directives policies regulations standards and guidance. Reviews and updates the current.
Nearly all applications that deal with financial privacy safety or defense include some form of access authorization control. The following mappings are to the nist sp 800 53 rev. An access control policy that addresses purpose scope roles responsibilities management commitment coordination among organizational entities and compliance. The following article details how the azure blueprints nist sp 800 53 r4 blueprint sample maps to the nist sp 800 53 r4 controls.
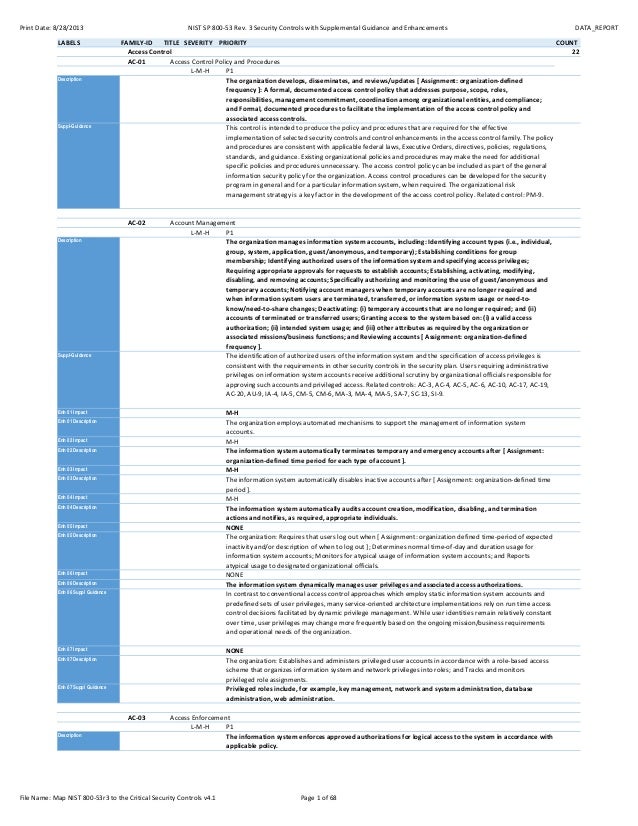
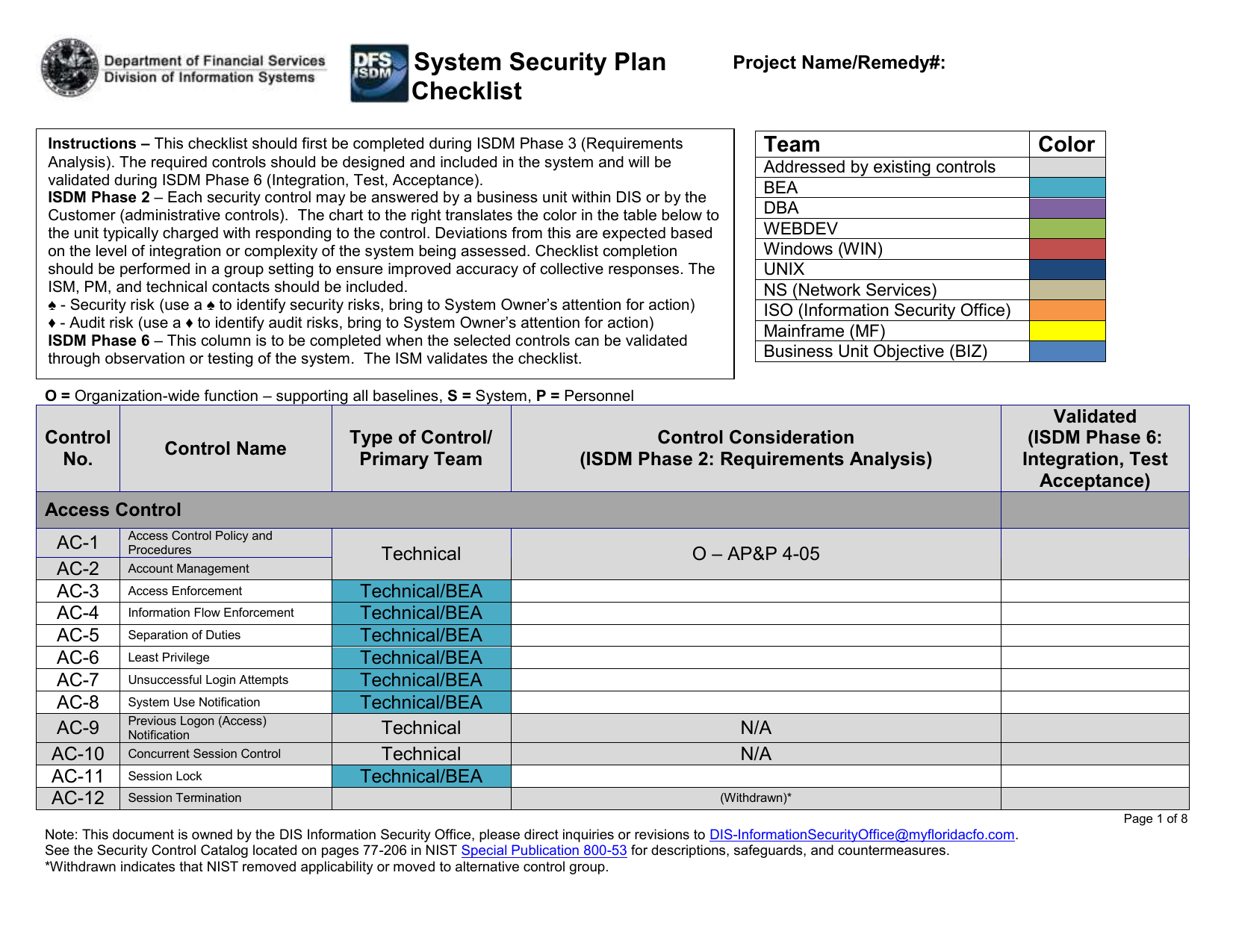
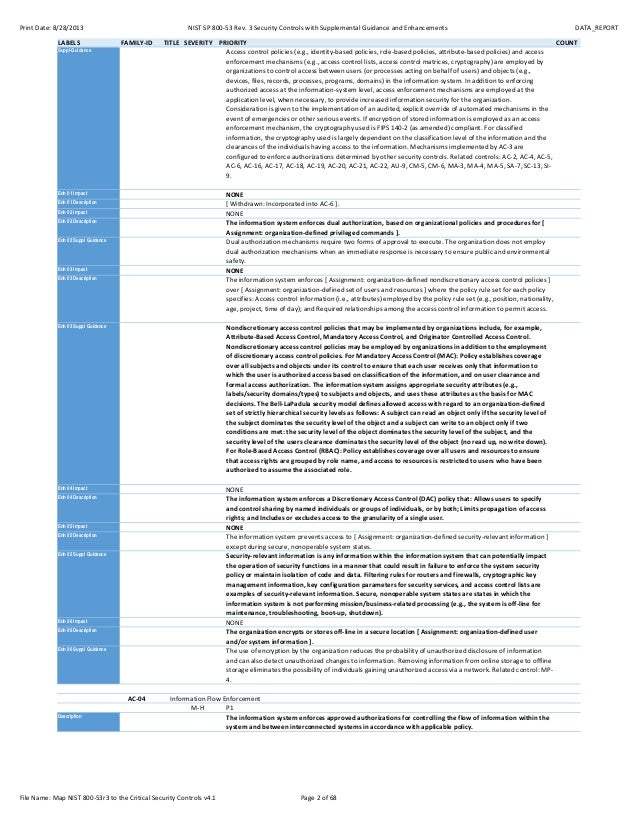
Access control is concerned with determining the allowed activities of legitimate users mediating every attempt by a user to access a resource in the system. P1 the information system enforces approved authorizations for logical access to the system in accordance with applicable policy. The organizational risk management strategy is a key factor in the development of the access control policy. Adequate security of information and information systems is a fundamental management responsibility.
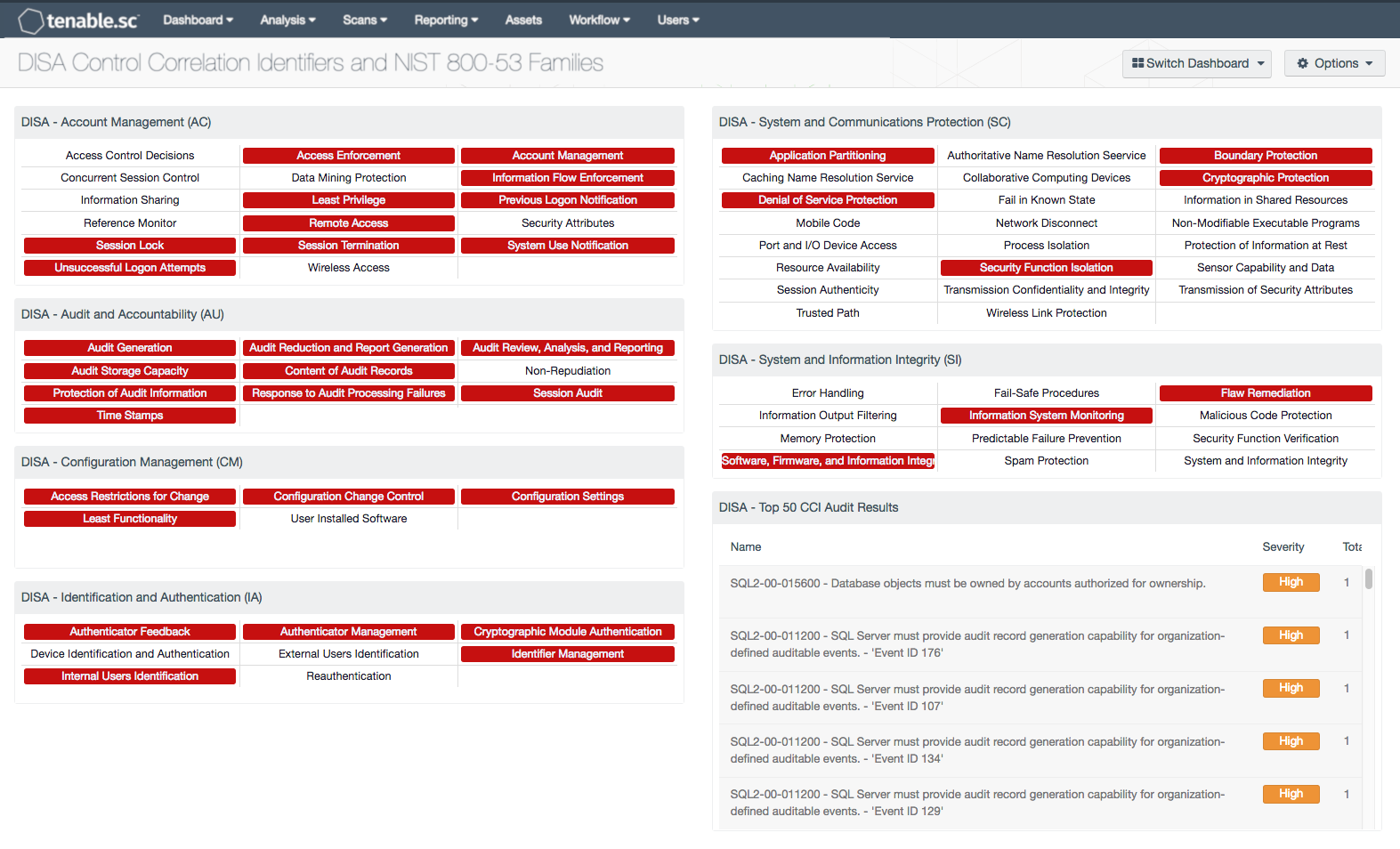
The federal identity credential and access management program provides implementation guidance for identity credential and access management capabilities for physical access control systems. Nist special publication 800 53 rev. Nist 800 100 nist 800 12 technical access control ac 2. Use the navigation on the right to jump directly to a specific control mapping.