Cyber Threat Intelligence Report Template

Cyber threat intelligence is a state of mind 18 take the data from the vendors augment it with your own internal data.
Cyber threat intelligence report template. Threat intelligence report sample. Overall the threat posture assessed as elevated1. Powerpoint proposal template a4 format author. This is a set of templates based on the templates created in sapho to help track and share cyber threat intelligence using open source collaboration software such as a wiki.
The use of these frameworks helps guide threat intelligence gathering efforts and inform incident response actions. The following blog post is a summary of a rfun 2017 customer presentation featuring brian scavotto cyber threat intelligence manager at fannie mae. Weekly threat intelligence report template. Threat intelligence monitoring and reporting sample report dwdocx.
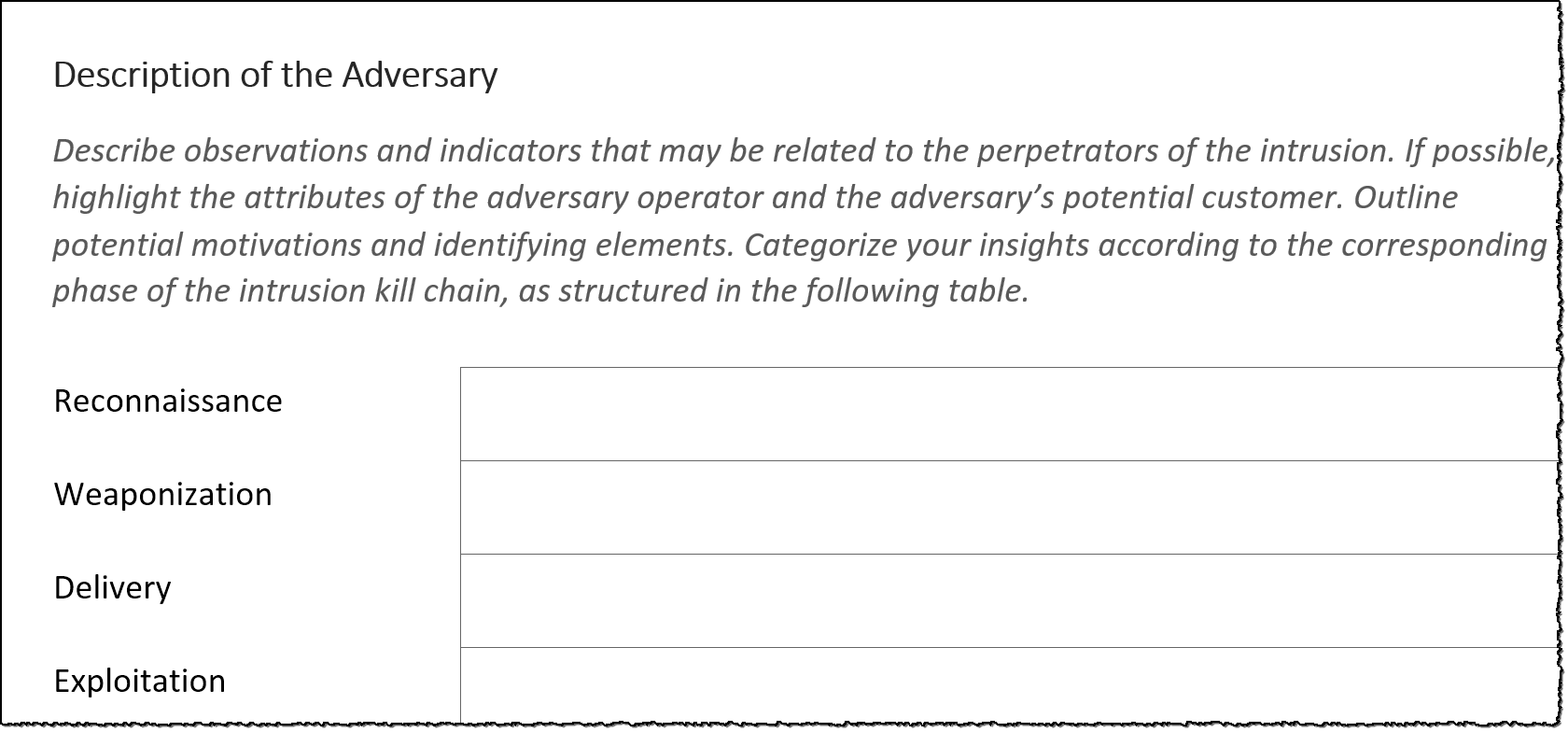
This template leverages several models in the cyber threat intelligence cti domain such as the intrusion kill chain campaign correlation the courses of action matrix and the diamond model. Cyber threat intelligence is more than data and technology c it is analyst expertise78 reoned methodologies and processdrinen integration the breadth and diversity of cti value is not realized when investment is exclusively in data and technology such as threat intelligence feeds or intelligence platforms. How to build a cyber threat intelligence team and why technology isnt enough october 26 2017 rfsid. Fireeye regularly publishes cyber threat intelligence reports that describe the members of advanced persistent threat apt groups how they work and how to recognize their tactics techniques and procedures.
Client specific threat areas the cyber intelligence collected and analyzed for client 1 suggests there is are a number of issues to be resolved. A state of mind. March 5 2019 parker crucq. Once considered weak in nature compared to other offenses cyber attacks are now potential weapons of destruction and are considered as high power tools of massive attacks.
Armed forces now increasingly rely on networks systems and servers for communications and information so. The growing number of cyber threats highlight the risks that us critical infrastructure and special forces face. These are intendend to track various events actors malicious code and other elements common to sophisticated intrusions. Randy armknecht cissp ence protiviti.